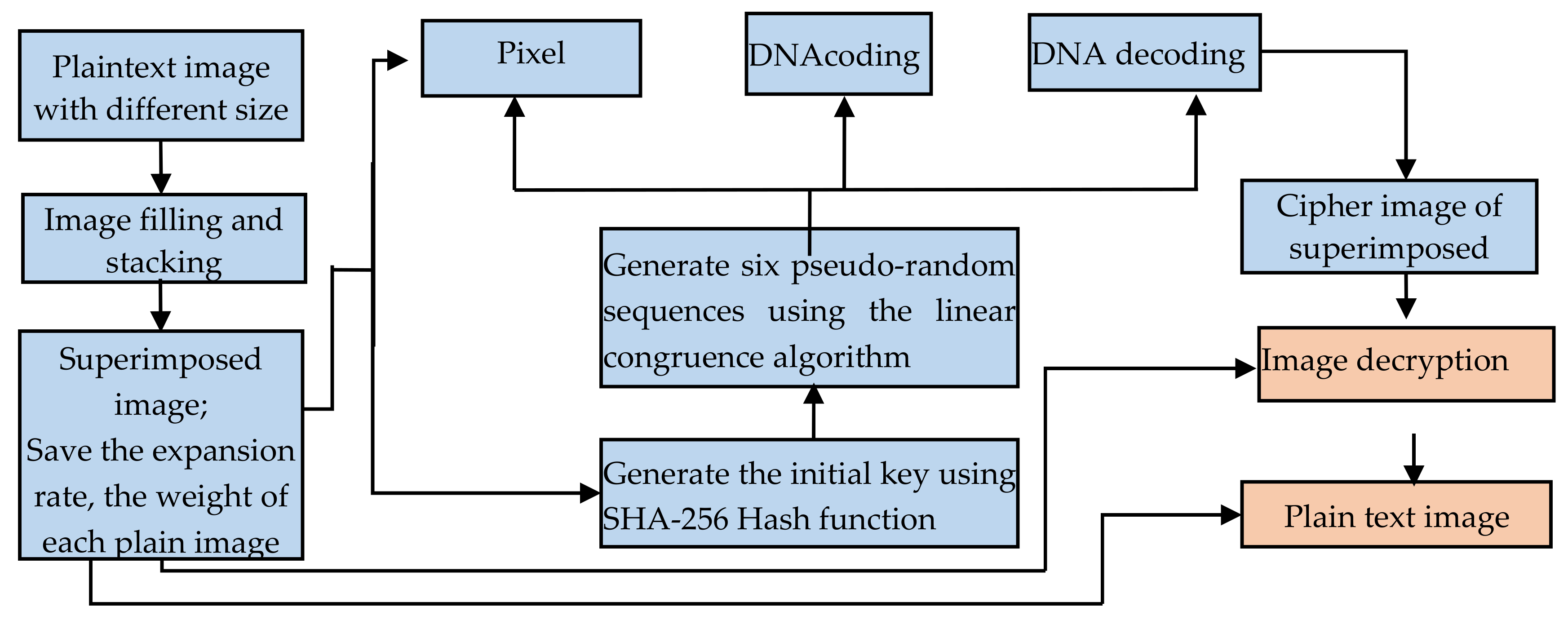
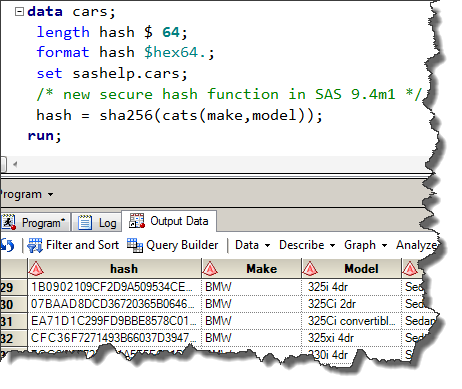
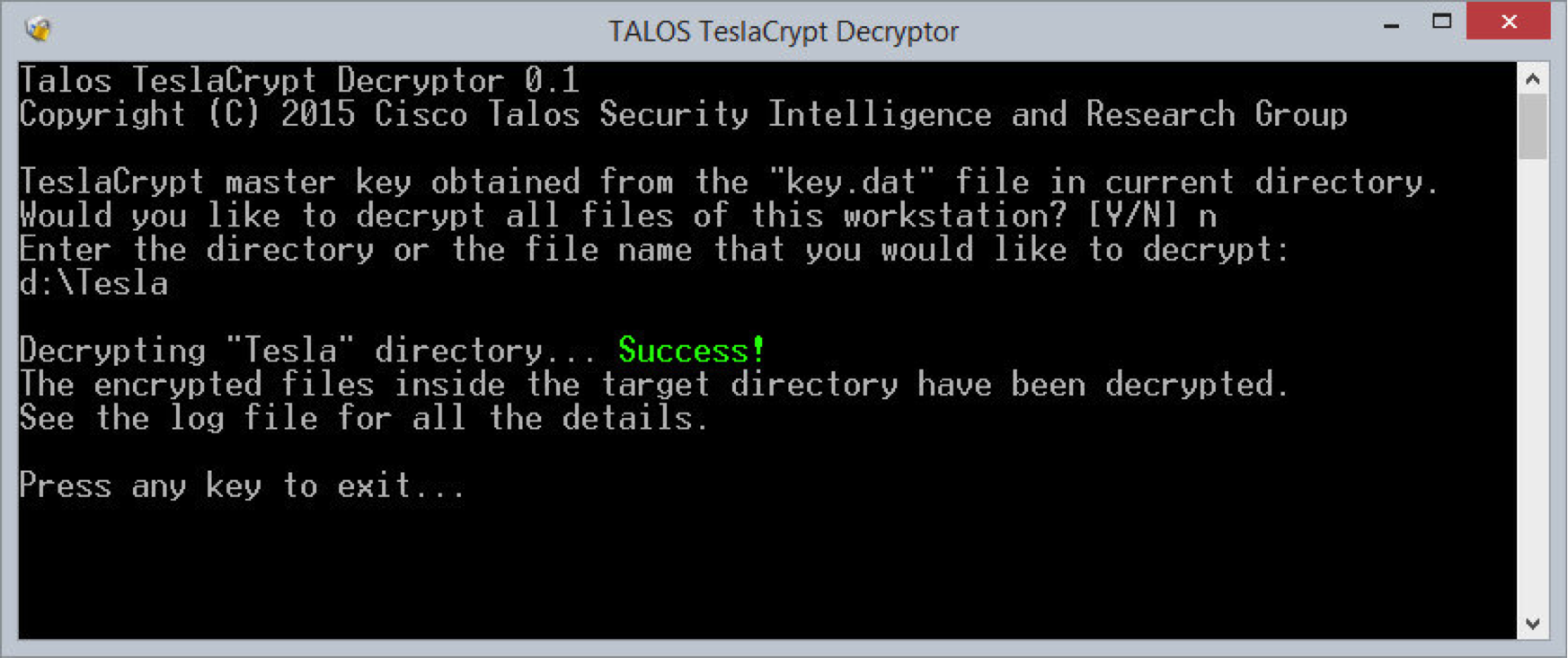
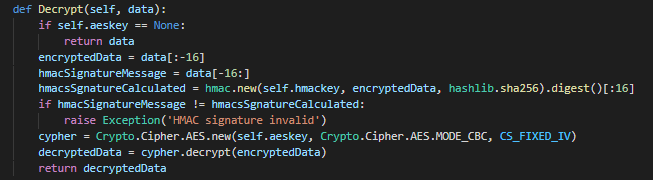
Multimedia stream hashing: A forensic method for content verification - Wales - 2023 - Journal of Forensic Sciences - Wiley Online Library

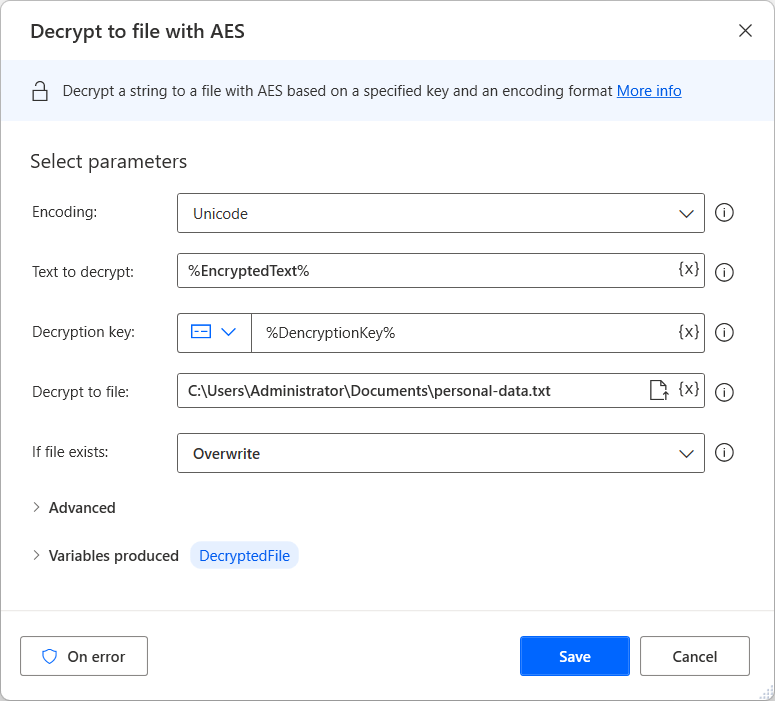
Secure Your Data with AES sha256 bit Encryption and Decryption method using PHP | by Deepak Singh | Medium